Debian OMV snapd 安装Certbot获取SSL证书 无需nginx apache 使用DNS TXT
Debian安装Certbot获取SSL证书
安装snapd
# 安装snapd
apt-get update
apt-get install snapd
# 安装 snapd core
snap install core
snap refresh core通过snapd安装certbot
snap install --classic certbot
# 软链接
ln -s /snap/bin/certbot /usr/bin/certbot如果遇到无法下载,可能需要翻墙,请给snap设置代理:
sudo snap set system proxy.http=http://127.0.0.1:1081
sudo snap set system proxy.https=http://127.0.0.1:1081获取SSL证书
执行certbot certonly
certbot certonly -d "*.youdomain.com" --manual --preferred-challenges dns-01 --server https://acme-v02.api.letsencrypt.org/directoryroot@docker00:/usr/bin# certbot certonly -d "*.youdomain.com" --manual --preferred-challenges dns-01 --server https://acme-v02.api.letsencrypt.org/directory
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator manual, Installer None
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel): xxx@xxx.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: N
Account registered.
Requesting a certificate for *.youdomain.com
Performing the following challenges:
dns-01 challenge for youdomain.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name
_acme-challenge.youdomain.com with the following value:
<your_dns_txt_value>
Before continuing, verify the record is deployed.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/youdomain.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/youdomain.com/privkey.pem
Your certificate will expire on 2021-07-01. To obtain a new or
tweaked version of this certificate in the future, simply run
certbot again. To non-interactively renew *all* of your
certificates, run "certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
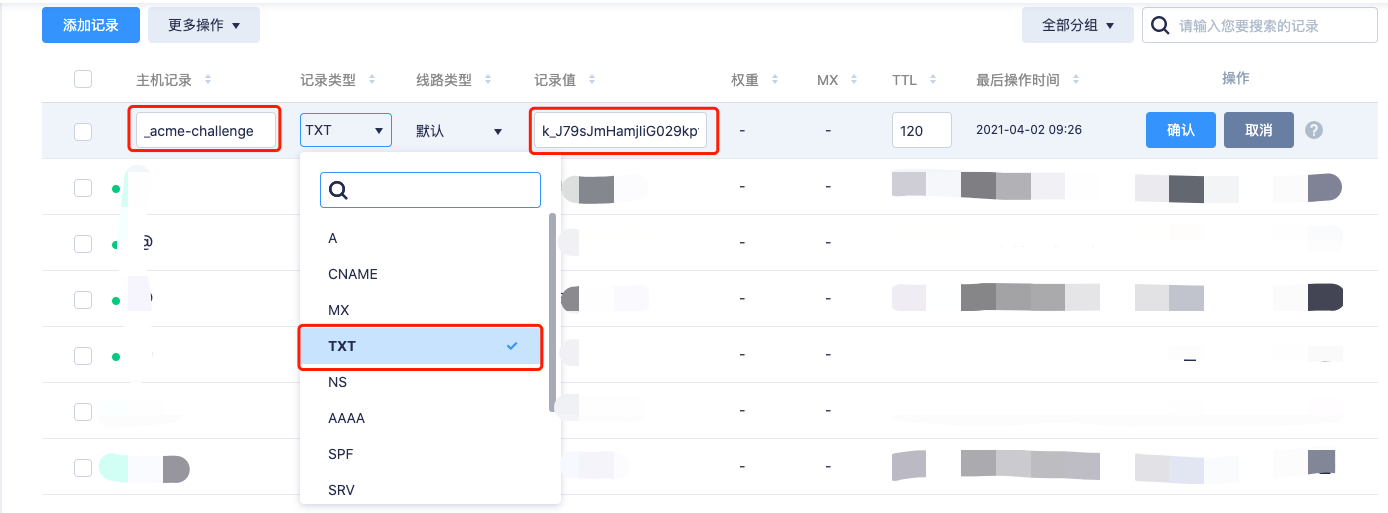
Donating to EFF: https://eff.org/donate-le添加DNS TXT记录
上面会通过获取DNS TXT验证域名是否是本人所有,进入域名管理中添加该记录
主机记录:_acme-challenge
记录类型:TXT
记录值:<your_dns_txt_value>(此处根据实际值进行替换)
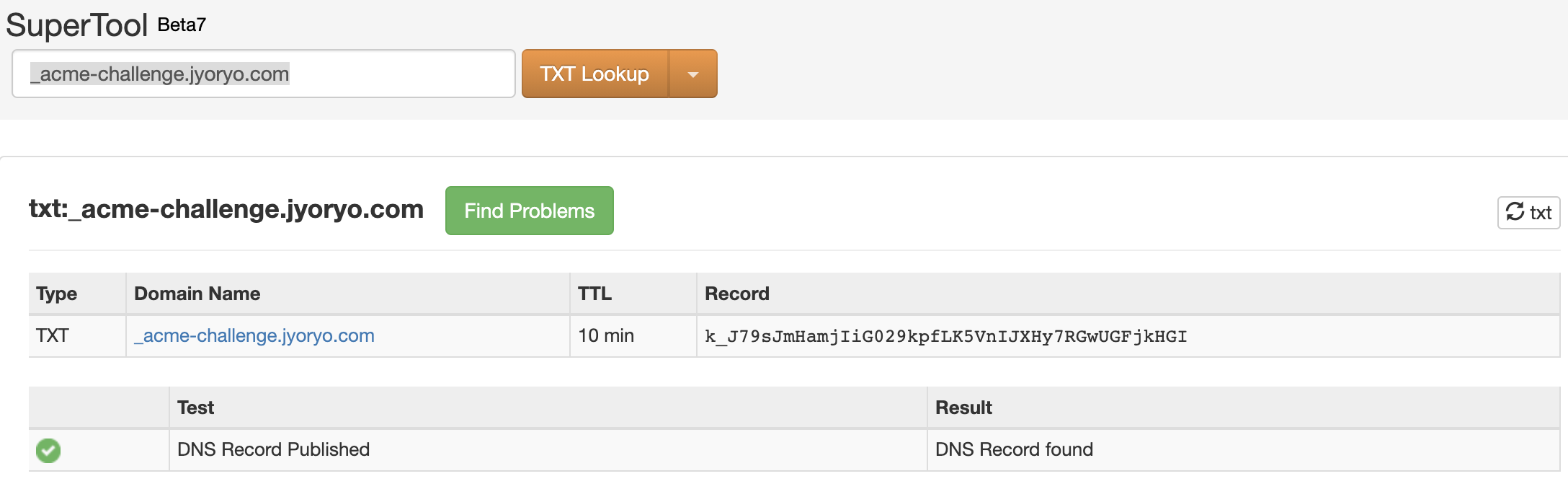
手工验证DNS TXT记录
工具网站:https://mxtoolbox.com/TXTLookup.aspx
填写:_acme-challenge.youdomain.com
拷贝证书
手工方式
进入生成的证书目录:
cd /etc/letsencrypt/live/youdomain.com/root@docker00:/usr/bin# cd /etc/letsencrypt/live/youdomain.com/
root@docker00:/etc/letsencrypt/live/youdomain.com# ll
total 4
lrwxrwxrwx 1 root root 34 Apr 2 09:23 cert.pem -> ../../archive/youdomain.com/cert1.pem
lrwxrwxrwx 1 root root 35 Apr 2 09:23 chain.pem -> ../../archive/youdomain.com/chain1.pem
lrwxrwxrwx 1 root root 39 Apr 2 09:23 fullchain.pem -> ../../archive/youdomain.com/fullchain1.pem
lrwxrwxrwx 1 root root 37 Apr 2 09:23 privkey.pem -> ../../archive/youdomain.com/privkey1.pem
-rw-r--r-- 1 root root 692 Apr 2 09:23 README拷贝并重命名
cp fullchain.pem /root/youdomain.com.cert
cp privkey.pem /root/youdomain.com.key
# 设置权限
chmod 644 /root/youdomain.com.cert /root/youdomain.com.key
# 将证书复制至目标服务器
cd /root
scp -P <port> youdomain.com.cert youdomain.com.key <user>@<host>:/tmp/接着通过ssh登录目标服务替换新的ssl证书并生效即可。
使用Shell脚本
在生成证书机器执行:
#!/bin/bash
sourceFolder='/etc/letsencrypt/live/youdomain.com'
sourceCertFile='fullchain.pem'
sourceKeyFile='privkey.pem'
targetFolder='/tmp'
targetCertFile='youdomain.com.cert'
targetKeyFile='youdomain.com.key'
# copy cert and key files
scp -P <port> ${sourceFolder}/${sourceCertFile} <user>@<host>:${targetFolder}/${targetCertFile}
scp -P <port> ${sourceFolder}/${sourceKeyFile} <user>@<host>:${targetFolder}/${targetKeyFile}
# 可选:直接调用服务器脚本执行,如果不方便,可以直接连上服务器端进行执行脚本
# ssh -p <port> <user>@<host> "<script_folder>/letsencrypt_update.sh"服务器端脚本:
#!/bin/bash
targetFolder='/tmp'
# 证书 youdomain.com
# certFile='youdomain.com.cert'
# keyFile='youdomain.com.key'
targetCertFile='youdomain.com.cert'
targetKeyFile='youdomain.com.key'
sslCertFile='/data/soft/nginx/conf/cert/youdomain.com/youdomain.com.cert'
sslKeyFile='/data/soft/nginx/conf/cert/youdomain.com/youdomain.com.key'
if [ -f "${targetFolder}/${targetCertFile}" -a -f "${targetFolder}/${targetKeyFile}" ]; then
cat ${targetFolder}/${targetCertFile} > ${sslCertFile}
cat ${targetFolder}/${targetKeyFile} > ${sslKeyFile}
rm -f ${targetFolder}/${targetCertFile}
rm -f ${targetFolder}/${targetKeyFile}
fi
# 多个证书可以类似添加
# 证书 frp.youdomain.com
# certFile='frp.youdomain.com.cert'
# keyFile='frp.youdomain.com.key'
targetCertFile='frp.youdomain.com.cert'
targetKeyFile='frp.youdomain.com.key'
sslCertFile='/data/soft/nginx/conf/cert/frp.youdomain.com/frp.youdomain.com.cert'
sslKeyFile='/data/soft/nginx/conf/cert/frp.youdomain.com/frp.youdomain.com.key'
if [ -f "${targetFolder}/${targetCertFile}" -a -f "${targetFolder}/${targetKeyFile}" ]; then
cat ${targetFolder}/${targetCertFile} > ${sslCertFile}
cat ${targetFolder}/${targetKeyFile} > ${sslKeyFile}
rm -f ${targetFolder}/${targetCertFile}
rm -f ${targetFolder}/${targetKeyFile}
fi
# 重启nginx使ssl证书生效
/data/soft/nginx/sbin/nginx -s reload
收藏,好好学习